Diskutil
Encrypting a complete disk under ML
20.01.13 Filed in: MacOS
By chance I came across an article (don’t have a link anymore, sorry) that showed how to completely encrypt a disk under Mountain Lion if that disk isn’t the one that was booted from. I have a MacBook Pro with an SSD in the regular SATA mount and a 640GB hard disk mounted in place of the DVD drive (see here for the story on that).
For quite some time, I’d been using an encrypted DMG that would mount as a data drive for my more sensitive files, but that is quite a pain in the rear end. For one thing, you need to figure out how much space you need, because you have to pick a finite size for the DMG as you create it. So either it wastes (a lot of) disk space when not filled up or you end up having to create a bigger one and moving all your files from one to the other if it gets too small.
The advantages of a hard disk that is completely encrypted are obvious since Lion, which introduced FileVault for the primary disk. Getting secondary disks to be encrypted under ML is not an issue if you’re formatting them - FileVault 2 takes care of that with a click in the selection list:
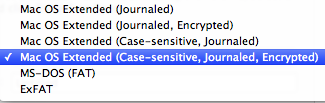
I’ve done this with another drive I have and it worked like a charm. But what to do if you have a 640GB drive nearly 90% filled with stuff you don’t want to be moving someplace else so that you can re-format your drive?
Well, as it turns out, there is a way to do this from the command line using diskutil - see this article. As the article states, it really does take VERY LONG to do this on-the-fly encryption. At first, I was a bit uneasy, as nothing seemed to happen, but there is a way to check on progress and after a good 20 hours, my drive was encrypted.
You can check how things are progressing with diskutil cs list, which gives you a list of all devices, including the current disk chunk converted:
| +-> Logical Volume Family 5C25AA1F-0EBE-49A6-A644-BBDBF988E421
| ----------------------------------------------------------
| Encryption Status: Unlocked
| Encryption Type: AES-XTS
| Conversion Status: Converting
| Conversion Direction: forward
| Has Encrypted Extents: Yes
| Fully Secure: No
| Passphrase Required: Yes
| |
| +-> Logical Volume C52CBE5D-0065-467E-A180-6512A52CB46F
| ---------------------------------------------------
| Disk: disk3
| Status: Online
| Size (Total): 638939721728 B (638.9 GB)
| Size (Converted): 392502968320 B (392.5 GB)
| Revertible: Yes (unlock and decryption required)
| LV Name: Macintosh HD
| Volume Name: Macintosh HD
| Content Hint: Apple_HFS
The converted drive works like a charm, I didn’t notice any slow-down of my system afterwards.
The only caveat - at least I haven’t found a solution yet - is that if you have moved your user folder to this drive (which is the sensible thing to do if you have a small SSD that you boot from and a large HDD to keep data on), you will have to create an admin account that you can use to unlock the HDD after a reboot.
I.e.: log into the admin account, unlock the HDD (ideally saving the password in the admin’s keychain), then log out and log into your regular account.
Not a big issue, really.
For quite some time, I’d been using an encrypted DMG that would mount as a data drive for my more sensitive files, but that is quite a pain in the rear end. For one thing, you need to figure out how much space you need, because you have to pick a finite size for the DMG as you create it. So either it wastes (a lot of) disk space when not filled up or you end up having to create a bigger one and moving all your files from one to the other if it gets too small.
The advantages of a hard disk that is completely encrypted are obvious since Lion, which introduced FileVault for the primary disk. Getting secondary disks to be encrypted under ML is not an issue if you’re formatting them - FileVault 2 takes care of that with a click in the selection list:

I’ve done this with another drive I have and it worked like a charm. But what to do if you have a 640GB drive nearly 90% filled with stuff you don’t want to be moving someplace else so that you can re-format your drive?
Well, as it turns out, there is a way to do this from the command line using diskutil - see this article. As the article states, it really does take VERY LONG to do this on-the-fly encryption. At first, I was a bit uneasy, as nothing seemed to happen, but there is a way to check on progress and after a good 20 hours, my drive was encrypted.
You can check how things are progressing with diskutil cs list, which gives you a list of all devices, including the current disk chunk converted:
| +-> Logical Volume Family 5C25AA1F-0EBE-49A6-A644-BBDBF988E421
| ----------------------------------------------------------
| Encryption Status: Unlocked
| Encryption Type: AES-XTS
| Conversion Status: Converting
| Conversion Direction: forward
| Has Encrypted Extents: Yes
| Fully Secure: No
| Passphrase Required: Yes
| |
| +-> Logical Volume C52CBE5D-0065-467E-A180-6512A52CB46F
| ---------------------------------------------------
| Disk: disk3
| Status: Online
| Size (Total): 638939721728 B (638.9 GB)
| Size (Converted): 392502968320 B (392.5 GB)
| Revertible: Yes (unlock and decryption required)
| LV Name: Macintosh HD
| Volume Name: Macintosh HD
| Content Hint: Apple_HFS
The converted drive works like a charm, I didn’t notice any slow-down of my system afterwards.
The only caveat - at least I haven’t found a solution yet - is that if you have moved your user folder to this drive (which is the sensible thing to do if you have a small SSD that you boot from and a large HDD to keep data on), you will have to create an admin account that you can use to unlock the HDD after a reboot.
I.e.: log into the admin account, unlock the HDD (ideally saving the password in the admin’s keychain), then log out and log into your regular account.
Not a big issue, really.
Comments